1.2.What is a Protocol?
Now that we've got a bit of a feel for what the "Internet" is, let's consider
another important word is the title of this book: "protocol." What
is
a protocol? What does a protocol do? How would you recognize
a protocol if you met one?
A Human Analogy
It is probably easiest to understand the notion of a computer network protocol
by first considering some human analogies, since we humans execute protocols
all of the time. Consider what you do when you want to ask someone for
the time of day. A typical exchange is shown in Figure 1.2-1. Human
protocol (or good manners, at least) dictates that one first offers a greeting
(the first "Hi" in Figure 1.2-1) to initiate communication with someone
else. The typical response to a "Hi" message (at least outside of New York
City) is a returned "Hi" message. Implicitly, one then takes
a cordial "Hi" response as an indication that one can proceed ahead and
ask for the time of day. A different response to the initial "Hi" (such
as "Don't bother me!", or "I don't speak English," or an unprintable
reply that one might receive in New York City) might indicate an unwillingness
or inability to communicate. In this case, the human protocol would
be to not ask for the time of day. Sometimes one gets no reponse at all
to a question, in which case one typically gives up asking that person
for the time. Note that in our human protocol, there are specific messages
we send, and specific actions we take in response to the received reply
messages or other events (such as no reply within some given amount of
time). Clearly, transmitted and received messages, and actions
taken when these message are sent or received or other events occur, play
a central role in a human protocol. If people run different protocols
(e.g., if one person has manners but the other does not, or if one understands
the concept of time and the other does not) the protocols do not
interoperate and no useful work can be accomplished. The same is
true in networking -- it takes two (or more) communicating entities running
the same protocol in order to accomplish a task.
Let's consider a second human analogy. Suppose you're in a college
class (a computer networking class, for example!). The teacher is
droning on about protocols and you're confused. The teacher stops
to ask, "Are there any questions?" (a message that is transmitted
to, and received by, all students who are not sleeping). You raise
your hand (transmitting an implicit message to the teacher). Your
teacher acknowledges you with a smile, saying "Yes ......." (a transmitted
message encouraging you to ask your question - teachers love to
be asked questions) and you then ask your question (i.e., transmit your
message to your teacher). Your teacher hears your question (receives
your question message) and answers (transmits a reply to you). Once
again, we see that the transmission and receipt of messages, and a set
of conventional actions taken when these mesages are sent and received,
are at the heart of this question-and-answer protocol.
Network Protocols
A network protocol is similar to a human protocol, except that the entities
exchanging messages and taking actions are hardware or software components
of a computer network, components that we will study shortly in the following
sections. All activity in the Internet that involves two or more
communicating remote entities is governed by a protocol. Protocols
in routers determine a packet's path from source to destination;
hardware-implemented protocols in the network interface cards of two physically
connected computers control the flow of bits on the "wire" between the
two computers; a congestion control protocol controls the rate at which
packets are transmitted between sender and receiver. Protocols are running
everywhere in the Internet, and consequently much of this book is about
computer network protocols.
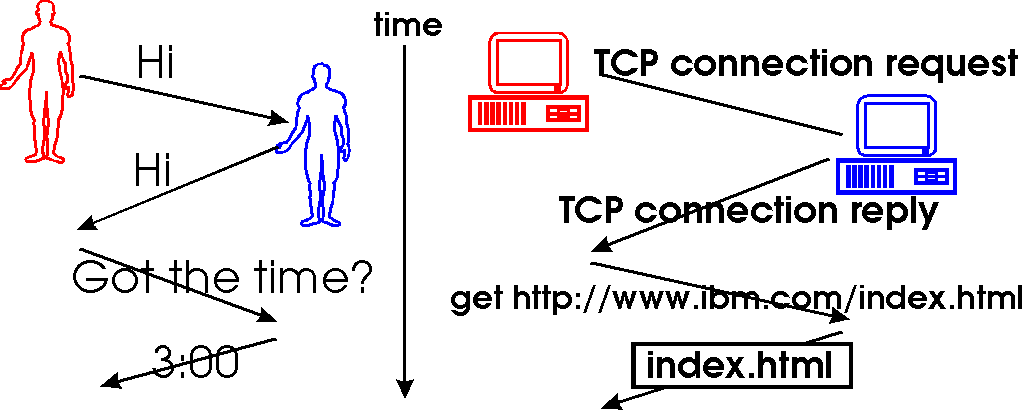
Figure 1.2-1: A human protocol and a computer network protocol
As an example of a computer network protocol with which you are probably
familiar, consider what happens when you make a request to a WWW server,
i.e., when you type in the URL of a WWW page into your web browser. The
scenario is illustrated in the right half of Figure 1.2-1. First, your
computer will send a so-called "connection request" message to the WWW
server and wait for a reply. The WWW server will eventually receive
your connection request message and return a "connection reply" message.
Knowing that it is now OK to request the WWW document, your computer then
sends the name of the WWW page it wants to fetch from that WWW server in
a "get" message. Finally, the WWW server returns the contents of
the WWW document to your computer.
Given the human and networking examples above, the exchange of
messages and the actions taken when these messages are sent and received
are the key defining elements of a protocol:
A protocol defines the format and
the order of messages exchanged between two or more communicating entities,
as well as the actions taken on the transmission and/or receipt of a message.
The Internet, and computer networks in general, make extensive use of
protocols. Different protocols are used to accomplish different communication
tasks. As you read through this book, you will learn that some protocols
are simple and straightforward, while others are complex and intellectually
deep. Mastering the field of computer networking is equivalent to understanding
the what, why and how of networking protocols.
Return
to Table Of Contents
Copyright Keith W. Ross and Jim
Kurose 1996-2000