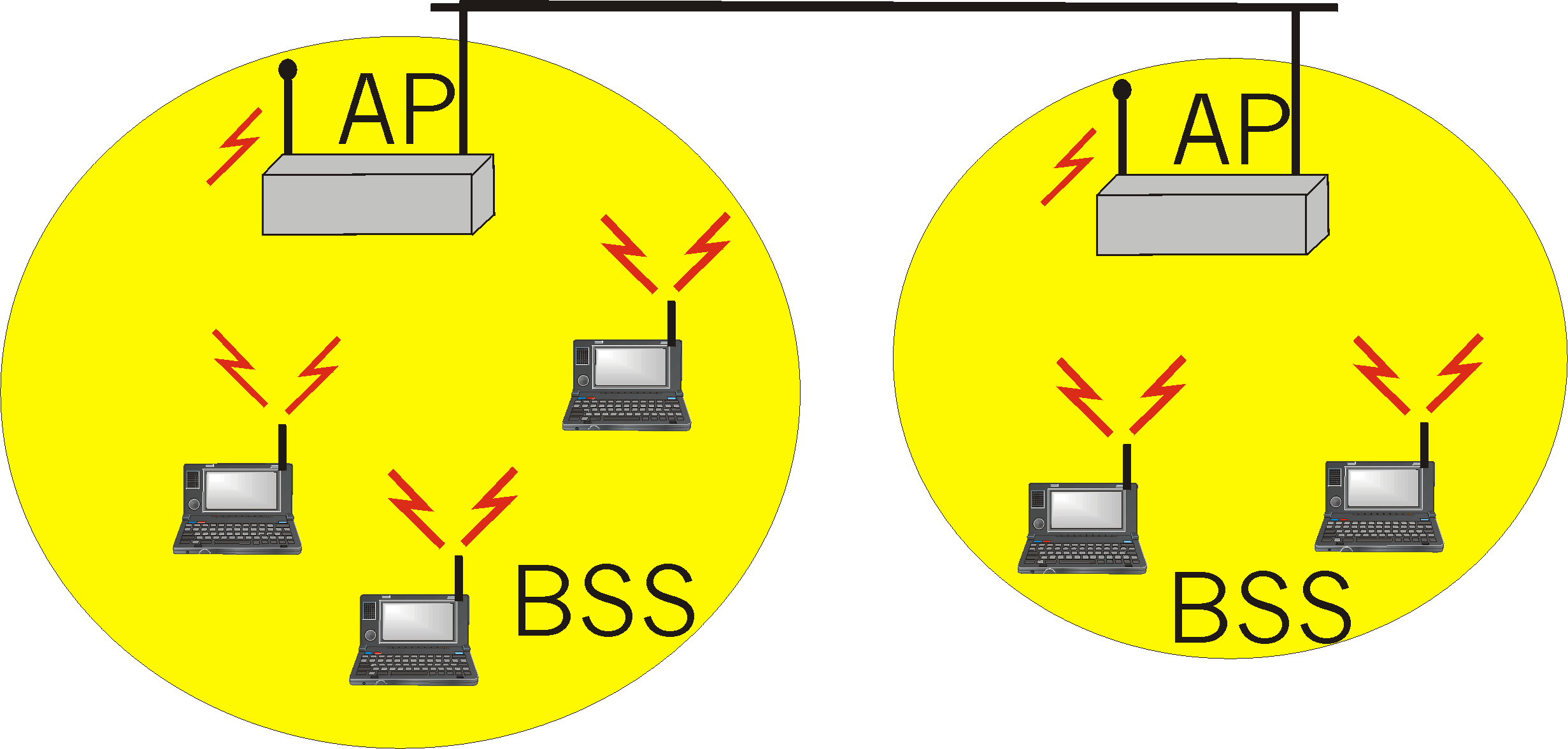
Figure 5.7-1: IEEE 802.11 LAN architecture

Figure 5.7-1 illustrates the principal components of the 802.11 wireless LAN architecture. The fundamental building block of the 802.11 architecture is the cell, known as the basic service set (BSS) in 802.11 parlance. A BSS typically contains one or more wireless stations and a central base station, known as an access point (AP) in 802.11 terminology. The stations, which may be either fixed or mobile, and the central base station communicate amongst themselves using the IEEE 802.11 wireless MAC protocol. Multiple APs may be connected together (e.g., using a wired Ethernet or another wireless channel) to form a so-called distribution system (DS). The DS appears to upper level protocols (e.g., IP) as a single 802 network, in much the same way that a bridged, wired 802.3 Ethernet network appears as a single 802 network to the upper layer protocols.
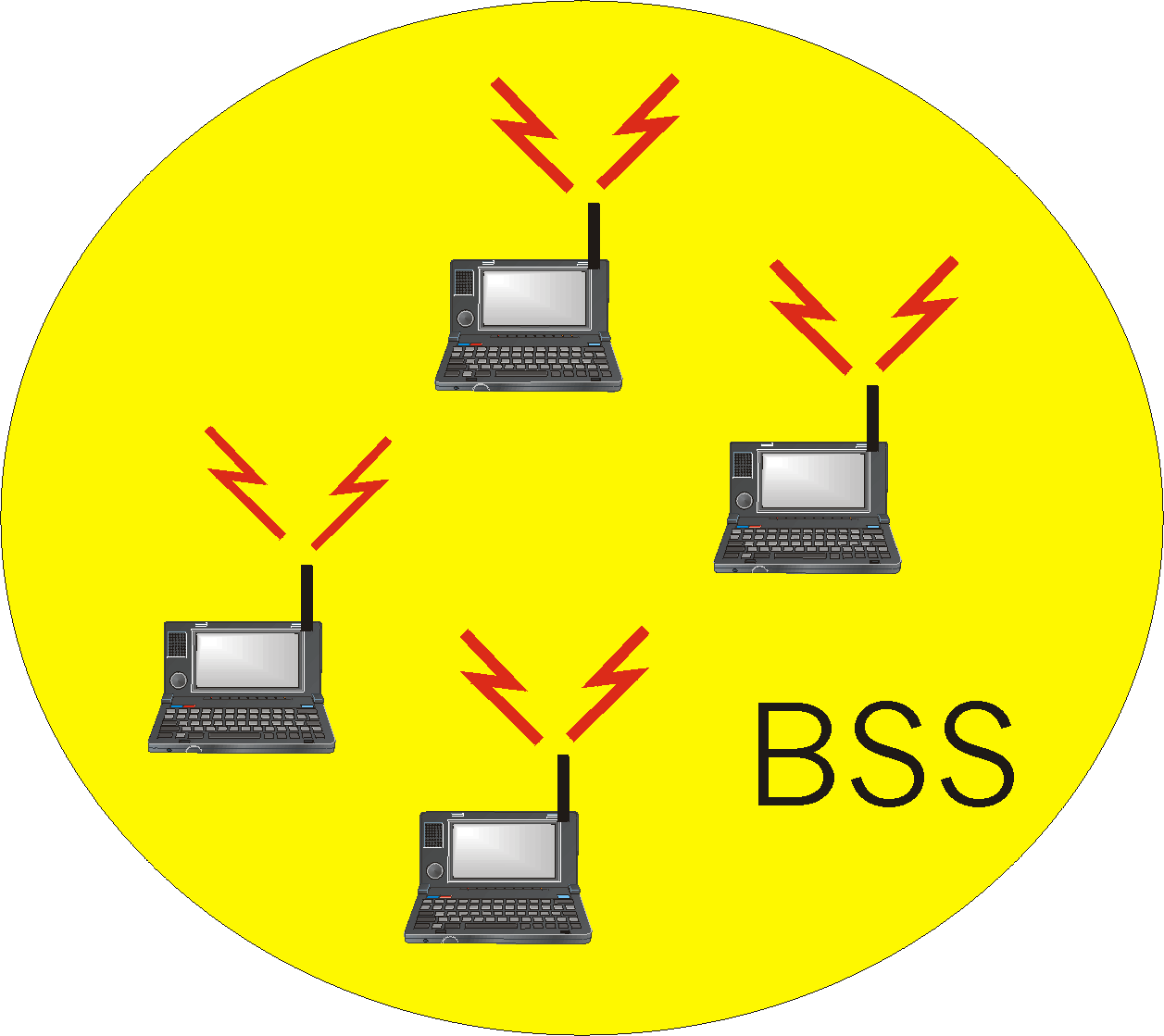
Figure 5.7-2 shows that IEEE 802.11 stations can also group themselves
together to form an ad hoc network - a network with no central control
and with no connections to the "outside world." Here, the network is formed
"on the fly," simply because there happen to be mobile devices that have
found themselves in proximity to each other, that have a need to
communication, and that find no pre-existing network infrastructure (e.g.,
a pre-existing 802.11 BSS with an AP) in the location. An ad hoc
network might be formed, for example, when people with laptops meet together
(e.g., in a conference room, a train, or a car) and want to exchange data
in the absence of a centralized AP. There has been a tremendous recent
increase in interest in ad hoc networking, as communicating portable devices
continue to proliferate. Within the IETF, activity in ad hoc networking
is centered around the
mobile ad hoc networks (manet) working group.
When a receiving station has correctly and completely received a frame for which it was the addressed recipient, it waits a short period of time (known as the Short Inter Frame Spacing - SIFS) and then sends an explicit acknowledgment frame back to the sender. This data link layer acknowledgment lets the sender know that the receiver has indeed correctly received the sender's data frame. We will see shortly that this explicit acknowledgment is needed because, unlike the case of wired Ethernet, a wireless sender can not itself determine whether or not its frame transmission was successfully received at the destination. The transmission of a frame by a sending station and its subsequent acknowledgment by the destination station is shown in Figure 5.7-3.
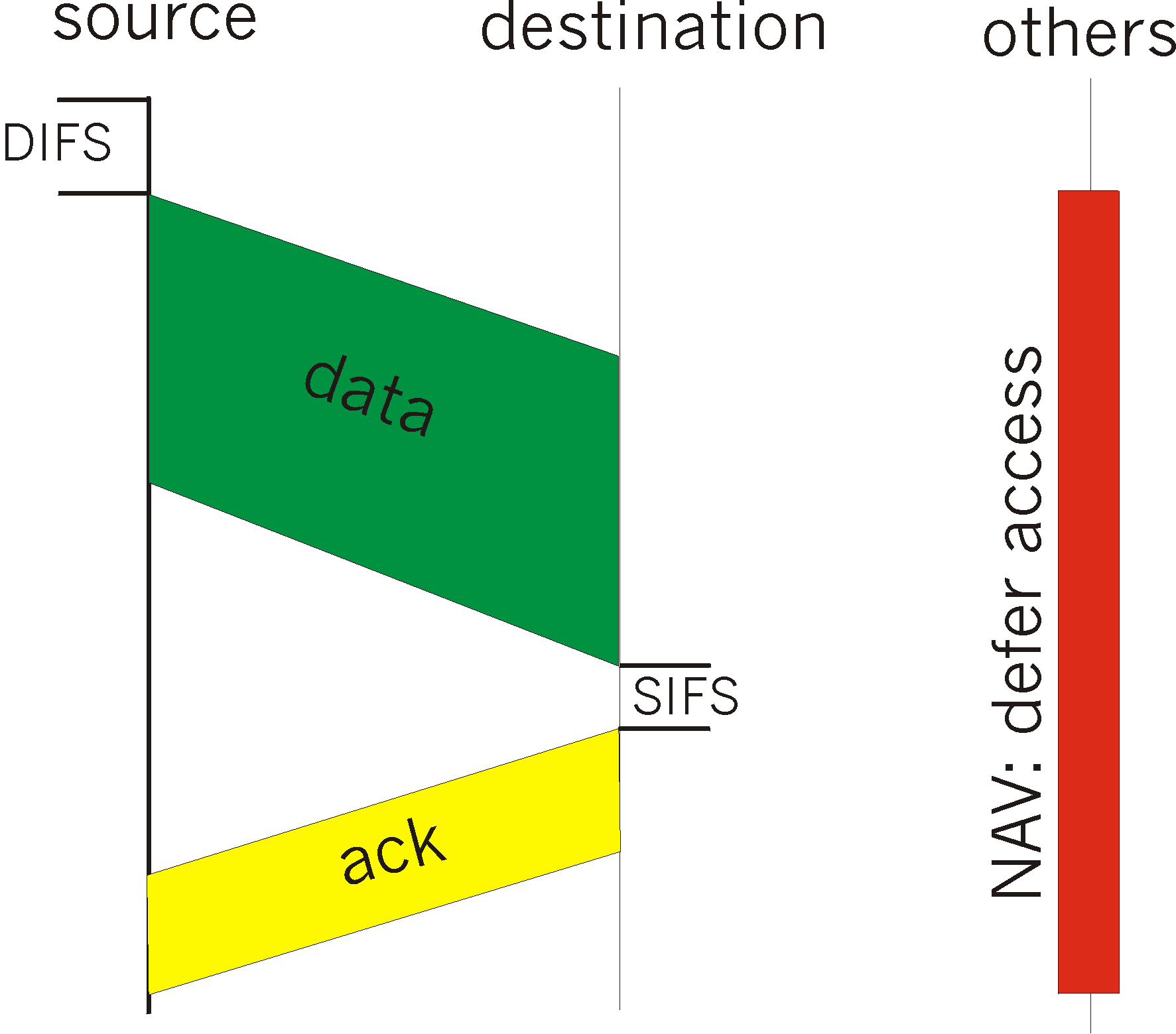
Figure 5.7-3 illustrates the case when the sender senses the channel to be idle. What happens if the sender senses the channel busy? In this case, the station performs a backoff procedure that is similar to that of Ethernet. More specifically, a station that senses the channel busy will defer its access until the channel is later sensed idle. Once the channel is sensed idle for an amount of time equal to DIFS, the station then computes an additional random backoff time and counts down this time as the channel is sensed idle. When the random backoff timer reaches zero, the station transmits its frame. As in the case of Ethernet, the random backoff timer serves to avoid having multiple stations immediately begin transmission (and thus collide) after a DIFS idle period. As in the case of Ethernet, the interval over which the backoff timer is randomizes is doubled each time a transmitted frame experiences a collision.
We noted above that unlike the 802.3 Ethernet protocol, the wireless 802.11 MAC protocol does not implement collision detection. There are a couple of reasons for this:
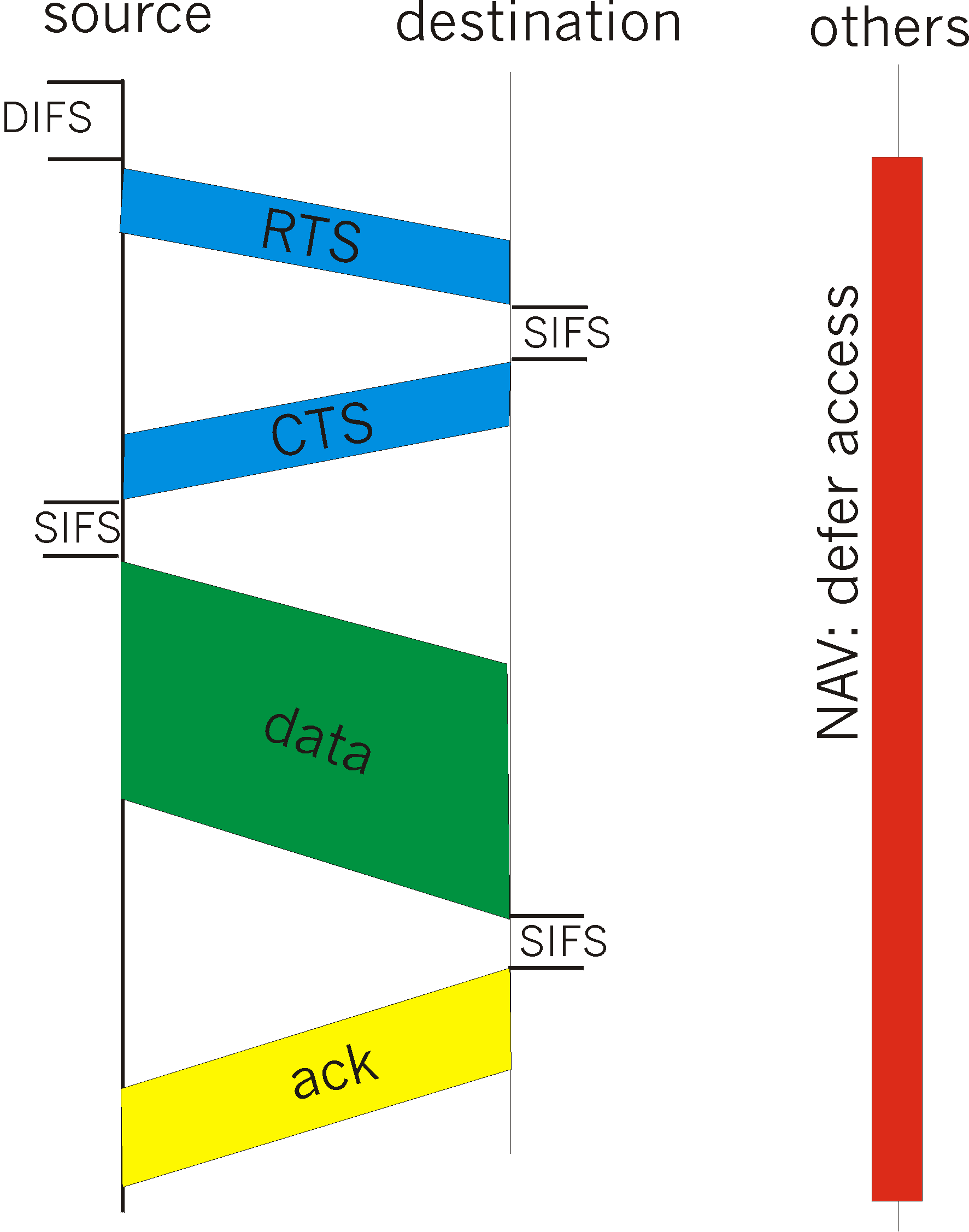
Given these difficulties with detecting collisions at a wireless receiver, the designers of IEEE 802.11 developed an access protocol which aimed to avoid collisions (hence the name CSMA/CA) , rather than detect and recover from collisions (CSMA/CD). First, the IEEE 802.11 frame contains a duration field in which the sending station explicit indicates the length of time that its frame will be transmitting on the channel. This value allows other stations to determine the minimum amount of time (the so-called network allocation vector, NAV) for which they should defer their access, as shown in Figure 5.7.3.
The IEEE 802.11 protocol can also use a short Request To Send (RTS) control frame and a short Clear To Send (CTS) frame to reserve access to the channel. When a sender wants to send a frame, it can first send a RTS frame to the receiver, indicating the duration of the data packet and the ACK packet. A receiver that receives an RTS frame responds with a CTS frame, giving the sender explicit permission to send. All other stations hearing the RTS or CTS then know about the pending data transmission and can avoid interfering with those transmissions. The RTS, CTS, DATA and ACK frames are shown in Figure 5.7-5. An IEEE 802.11 sender can operate either using the RTS/CTS control frames, as shown in Figure 5.7-5, or can simply send its data without first using the RTS control frame, as shown in Figure 5.7-3.
The use of the RTS and CTS frames helps avoid collisions in three important ways:
Copyright James F. Kurose and Keith W. Ross 1996-1999 . All rights reserved.